This article contains an alternative method to “FORCE MOBILE applications” to route all trafic using PPTP VPN and redirecting all traffic to BURP suite using transparent PROXY. However most of the times this is not a straight forward process.
Most of the problems come from the devices ability to accept or reject BURP suite certificates
this method does NOT REQUIRE A ROOTED / JAILED BREAKED device.
for this tutorial you will need:
- A linux distribution (e.x Kali Linux)
- PPTP server
- Burp suite community
- Android / IOS device
- ANDROID / IOS target app (if this is the device you are doing tests).
- Mobile device (ANDROID/IOS) and Linux machine should be in the same network (LAN)
STEP 1: Install all dependencies
This is a BASH script that is going to help you to install all dependencies and setup PPTP VPN.
This script:
- Install PPTP server
- Set up username and password (VPN)
- Allow port forwarding
- start PPTP server
- Create IPTABLES rules to redirect 80 and 443 trafic to BRUP
- setup VPN network.
this script should be run only once. This is the output of the script
at the end there are some IPTABLES RULES that are REQUIRED TO EXECUTE with sudo. THESE RULES MUST BE RUN each time the PPTP service is started.
STEP 2: INSTALL BURP SUITE CERTIFICATES (as user)
STEP 3: SET UP BURP SUITE
Make BURP SUITE listen to “all interfaces” on port 8080 on your local machine.
The next step is REALLY IMPORTANT please make sure to select this option, otherwise it is not going to work.
Make sure BURP has this config:
Since Android Nougat, Android no longer trusts user or admin supplied CA certificates
STEP 3: CONNECT TO PPTP from your ANDROID / IOS DEVICE
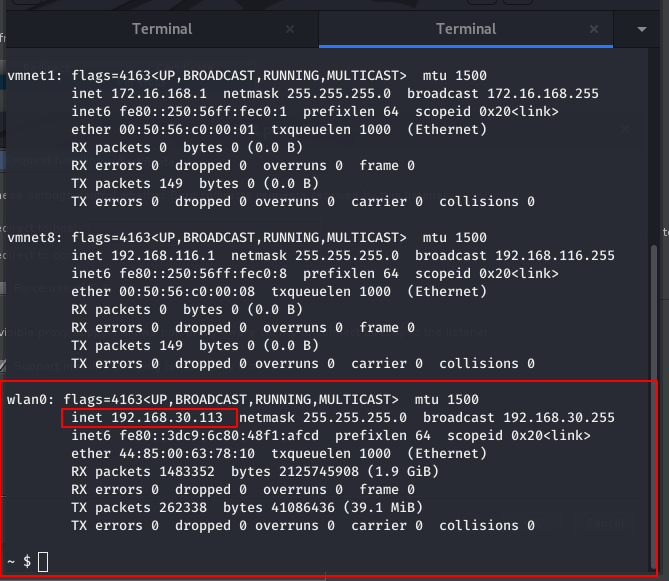
check your LINUX MACHINE IP
This is the ip that is required that you need to SETUP in your PPTP VPN parameters
in your ANDROID DEVICE search VPN (Settings)
Add New PPTP VPN with your linux machine, usename and password defined in previous steps.
Then connect to the VPN by TOUCHING the VPN name (it might ask you for user name and password again)
Then you should be connected to your VPN.

STEP 4: INTERCEPT HTTP / HTTPS REQUESTS
Start to intercept HTTP / HTTPS traffic .
STEP 5: SCRIPT TO RUN EVERYDAY TO START PPTP AND TO GET IPTABLES RULES
Happy Hacking…